The Current State of Cybersecurity Challenges in Modern Iot Devices
Introduction
This paper aims to examine the development of the phenomenon known as the Internet of Things (IoT). It attempts to highlight the potential cybersecurity challenges of IoT applications, and the related ethical issues that such cybersecurity challenges introduce. The essay is developed with the use of secondary data, particularly peer-reviewed journals, and reliable online sources. The essay concludes with an overview of the current innovative technological solutions that have been proposed as cybersecurity solutions for IoT devices.
The Internet of Things (IoT)
The Internet of Things (IoT) refers to a collection of interconnected devices through either wireless or wired Internet connection (Tawalbeh et al., 2020). Recently, IoT devices have become more popular and are widely adopted in various industries and home settings. Such devices are also used for industrial applications, such as transportation systems and power plants. Furthermore, current trends and projects, such as Industry 4.0, have aided in developing sophisticated business models and improving the interconnectivity between organisations’ systems (Sadeghi et al., 2015). A device within the IoT system could, therefore, include a car, electronic device, or various other systems (Abomhara and Koein, 2015). The communication between such devices is made through hardware elements such as sensors, mobile applications, and actuators, which enable the elements to interconnect with the digital world. Figure 1 below highlights the key elements of an IoT system.
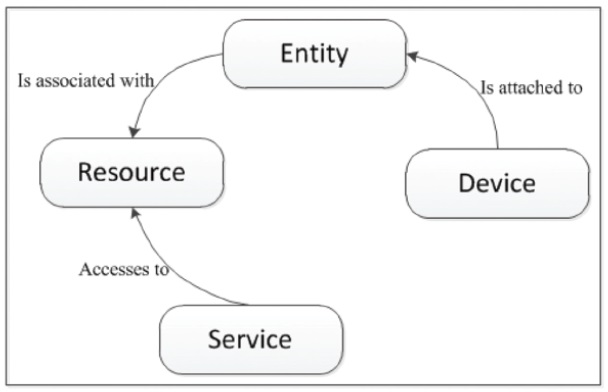
Figure 1: An example of an IoT System (Source: Abomhara and Koein, 2015)
Cybersecurity Challenges of IoT
The major diffusion of interconnected devices in an IoT system has increased the requirement for strong security measures in such systems. Particularly, IoT systems often amass a large volume of data, which is referred to as ‘Big Data’. Such data could include individuals’ and companies’ confidential information, and if accessed by unauthorised attackers, there could be major adverse impacts (Kumar and Patel, 2014).
Besides the increase in potential cyberattacks on IoT devices, there are also new and sophisticated tools accessible to attackers, which further improve the opportunities to gain unauthorised access to these devices. Thus, it is essential to investigate the potential cybersecurity solutions for IoT devices, to ensure that such devices can be successfully implemented and prevent vulnerabilities and threats. Some of the potential cyberattacks and vulnerabilities in IoT systems are further discussed in the next subsection.
1 Malware Injection
Malware refers to programming codes that are generated with the aim of conducting unauthorised or malicious activities (Karanja et al., 2017). IoT devices are susceptible to malware, which can be used by attackers to gain access to such devices or gain access to information stored on them. An example of the adverse impact of malware is the development of ransomware referred to as WannaCry, which was used for a cyberattack in 2017. The ransomware invaded various IoT devices in more than 100 countries and disrupted both corporate and government IoT networks and systems, which resulted in various negative outcomes (Brooks, 2021).
Other versions of malware programs, such as mirai and botnet have been developed for tailored cyberattacks on specific systems and networks. Such programs can also be used to identify default passwords on IoT devices, or access users’ systems remotely (Bertino and Islam, 2017). Malware programmers often design program obfuscation methods, such as metamorphism and polymorphism, which make it difficult to detect such attacks. Also, IoT devices are particularly more susceptible to these attacks because they are constantly connected to the Internet, unlike conventional standalone computer systems (Bertino and Islam, 2017).
2 Denial of Service Attacks
Denial of Service (DoS) attacks refer to cyberattacks whereby an attacker attempts to exhaustively consume all the available resources on a network. Thus, legitimate users are unable to gain access to such network or access information stored on their systems (Karanja et al., 2017). The Distributed Denial of Service (DDoS) is also like DoS, though this often includes a more coordinated attack, whereby an attacker attempts to use the resources of numerous network nodes. Both DoS and DDoS are major attack vectors for IoT systems, as attackers could gain access to such systems and flood them with various requests, thereby disabling services or slowing down the network’s performance.
Our Advantages
Quality Work
Unlimited Revisions
Affordable Pricing
24/7 Support
Fast Delivery